On Tuesday, a transnational cybersecurity company has trumped the discovery of a trailblazing Mac malware. According to Joshua Long, one of the online researchers who rooted out this second-gen ‘Mac-blaster”, revealed that this type of malware is quite unique, but very dangerous nonetheless.
Intego’s Proof-of-Concept showed that the exploit could masquerade as an Adobe Flash Player update. What’s even worse is that the viral payload was found on multiple websites, some of them being marked as high-ranking by Google’s search engine.
Will it Blend? The Macintosh Edition
So, we have a new type of malware to look out for. What’s the big deal about that? Or, better yet, how bad can it be? Very bad or so Joshua Long of Intego claims.
The malware, which is actually a nasty trojan, appears to be a rogue-like variant of the OSX\AMC (that would be Mac’s advanced cleaning system. Dubbed the OSX\CrescentCore (such a lovely and awe-inspiring name for a trojan), it’s what you may call a door opener for ransomware and other things that go bump the night.
Anyway, according to Long, CrescentCore can easily jump into your Mac if you’re not careful about updates. As far as the timeline is concerned, this trojan was first encountered by Long’s team while investigating several high-ranking websites on Google.
Apparently, the tipping point was a random quotation marks search of CrescentCore. The very first result was a seemingly high-ranking website called “GetComics” which, reportedly, offered the latest comic book issues completely free of charge.
Well, guess what? Instead of getting your free pdf copy, the malware will redirect you another website. Up next, your browser will bounce between several affiliate links, before ending up on the very wrong side of the Internet.
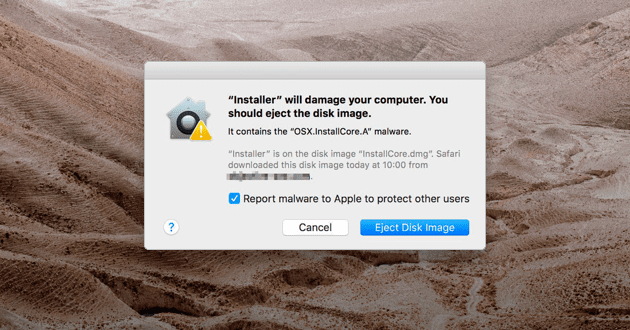
What happens there? Nothing much; your browser will automatically begin to download an installation package, supposedly to update the Adobe Flash Player extension to the latest version. If that wasn’t enough, the viral payload can also seep into your Mac if you click any “Install Adobe Flash Player” pop-up ad.
So, what happens once the installation process is completed? According to Long, when CrescentCore gets into your Mac, it will install a LaunchAgent in the machine’s library folder. From there, it can basically instruct your Mac on what types of codes to run on startup.
What happens after all these things unfold? Your guess is as good as mine: ransomware, more trojans, perhaps a couple of polymorphic viruses, just to spice things up.
Unfortunately, the news keeps getting worse – Long said that he and his team had a hard time isolating and reverse-engineering the malware since CrescentCore is capable of defending itself.
How do you ask? Normally, cybersecurity specialist uses VMs in order to analyze and get rid of the malware. Second-gen malware like this trojan is capable of scanning your Mac for VM software and AVs. If one or both is present on your system, the malware simply goes into a dormant state, waiting for its chance.
Wrap-up
Takeaways? The only thing that springs into mind would be to stay away from suspicious websites boasting free stuff and to refrain from clicking on pop-ups. Also, consider an AV\antimalware subscription for your machine. So, what’s your take on CrescentCore? Hit the comments section and let me know.
 Cyber Security Magazine
Cyber Security Magazine