Every computer forensic gumshoe needs a set of good, solid tools to undertake a proper investigation, and the tools you use vary according to the type of investigation you’re working on.
The list of tools isn’t all-inclusive — and you may have your own favourites — but the ones we describe are the basic ones you should use.
Computer Forensic Software Tools
The days of hard-core computer geeks knowing every square digital inch of an operating system are years behind us.
Although computer forensic professionals can now do the drudge work of scanning for evidence using nothing more than a keyboard and a hex editor, that person can access tools that automate the work to use their time more effectively.
In fact, modern computer forensic software can find evidence in only minutes, whereas in the “old days” the process took hours or even days! You still have to know your way around a computer, but these tools are true time-savers.
Just remember that a tool is only as good as the person who uses it.
EnCase
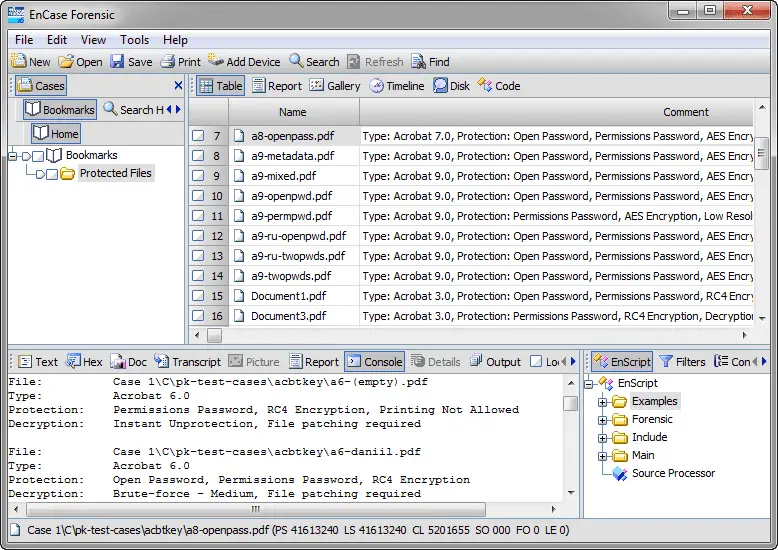
EnCase, the gold standard is used by countless organizations for almost any computer forensic investigation. The power of this must-have item for your computer forensic toolbox, and your ability to customize it for unique searches, set it apart from most competitors.
EnCase comes built-in with many forensic features, such as keyword searches, e-mail searches, and Web page carving. The numerous versions of its forensic software range from mobile device acquisitions to full-blown network forensic-analysis tools.
Two other cool features are its:
- Scripting language: You can customize searches.
- Fully automated report function: It builds reports for you quickly.
EnCase is sold by Guidance Software on its Web site. Support for EnCase is rock solid, and the technical support staff knows how to solve problems fairly quickly in addition to providing multilanguage support.
Forensic ToolKit (FTK)
AccessData has created a forensic software tool that’s fairly easy to operate because of its one-touch-button interface, and it’s also relatively inexpensive. The new version of FTK is even easier to use, and AccessData has started a forensic certification, ACE, based on its software.
FTK has automated, to a high degree, the hard, behind-the-scenes work of setting up searches. Press the Email button and out pop the e-mails. The FTK report generator does the hard work of putting a useful report into the forensic software’s automated hands while still allowing the investigator control over the report if needed.
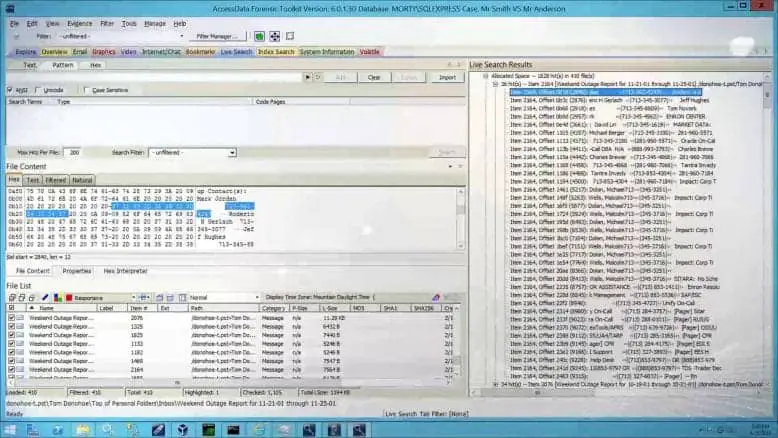
FTK is sold on the AcessData Web site at www.accessdata.com. Everything you need to order the software and training is on the site. Even the certification process is available for you to peruse.
Device Seizure
The Paraben forensic tools compete with the top two computer forensic software makers EnCase and FTK (described earlier in this chapter). Still, the company truly shines in the mobile forensic arena.
Using Paraben’s Device Seizure product, you can look at most mobile devices on the market. With more cases going mobile, Device Seizure is a must-have tool.
You can use Device Seizure to access and download almost all information contained in a mobile device, such as text messages or user data, and in a way that’s forensically acceptable in court.
Device Seizure and all the extras that can go with it are at www.paraben.com along with other useful forensic tools.
Computer Forensic Hardware
In contrast to computer forensic software designed to extract data or evidence on time and from a logical point of view, forensic hardware is primarily used to connect the computer’s physical parts to extract the data for use with the forensic software.
The basic idea behind forensic hardware is to facilitate the forensic transfer of digital evidence from one device to another as quickly as possible.
FRED
The Forensic Recovery of Evidence Device (FRED) forensic workstation from Digital Intelligence has an interface for all occasions — and then some. In addition to the laboratory version, FRED comes in mobile versions that facilitate the acquisition of evidence in the field for quick analysis.
FRED combines just about every available interface into one convenient workstation so that you don’t have to connect and disconnect a toolbox full of interfaces. Another helpful FRED feature is collecting software packages that are loaded on it if you request it: EnCase, FTK, Paraben’s P2, and many others.
Digital Intelligence, at www.digitalintelligence.com, has all the information you could ever want about the FRED systems. The company also offers training in the use of its systems and provides helpful technical support.
CRU Forensic Field Kit
When you need a small footprint and useful equipment for field use, the CRU field kit is hard to beat, figuratively and literally. Even with its small footprint, this field kit has the most popular interfaces available, and you can even customize it for your unique needs.
Using the CRU field kit, you can carry the essential pieces of your forensic toolkit. The heart of this field kit consists of the write-protect devices that WiebeTech manufactures in-house. The kits also contain interfaces for EIDE, SATA, and laptop hard drives.
You can find CRU field kits here, and they’re also listed at some third-party Web sites.
Logicube
Logicube offers some of the fastest disk-to-disk and disk-to-image transfer equipment now on the market. As storage devices grow larger, transferring 4 gigabytes per minute can save quite a bit of time over other field data acquisition methods.
The Logicube data capture equipment captures data from a target media. It transfers it to another disk or an image while at the same time performing an integrity check to ensure a forensic copy. The devices have various interfaces and usually come in a field kit configuration.
The Logicube Web site at www.logicube.com has information about the devices and how to order them. The company also offers other forensic products and has an in-house research-and-development team.
Computer Forensic Laboratories
Every good computer forensic scientist or investigator needs a place to do their work. In the ideal location to conduct an investigation, you have absolute control of security, tools, and even the physical environment.
Ideally, we’re describing your computer forensic laboratory! As in any science field, computer forensics requires its own set of laboratory tools to get the job done.
Computer forensic data server
Any computer forensic investigative unit of any size rapidly runs into where to store cases in progress or that need to be archived for possible later use. A centralized data storage solution is the best and most secure solution.
A forensic data server allows you to keep forensic images in a centralized, secure, and organized manner that lets you focus more on analyzing cases than looking for them. A server needs to have large data capacity, authenticate users for security purposes, and the capacity to perform backups of all data in case the storage devices fail.
You can find commercial-grade servers at any larger computer vendors, such as Dell and HP, and forensic companies, such as Digital Intelligence.
Forensic write blockers
One basic piece of equipment that a computer forensic laboratory needs are simple but effective write blocker. Although most software tools have built-in software write blockers, you also need an assortment of physical write blockers to cover as many situations or devices as possible.
A write blocker is used to keep an operating system from making any changes to the original or suspect media to keep from erasing or damaging potential evidence.
Software write blockers work at the operating system level and are specific to the operating system. In other words, a software write blocker works on only the operating system in which it is installed.
A physical write blocker works at the hardware level and can work with any operating system because, at the physical level, the write blocker is intercepting (or, in many cases, blocking) electrical signals to the storage device and has no concern about which operating system is in place.
The technology used by computers to read and write to storage devices is well understood and fairly straightforward — you can find dozens of manufacturers of write-protect devices.
For reliability and support, stick with these name brands in the industry:
- Digital Intelligence: The UltraKit write-block product (see www.digitalintelligence.com) follows the everything-but-the-kitchen-sink model. All standard storage device formats, such as IDE, SCSI, SATA, and USB, are supported. Besides, the cables and power supplies are furnished, to make this kit one of the most complete in the industry.
- Paraben: Paraben has taken the idea of a Faraday box and added silver-lined gloves to allow an investigator to work on a wireless device located inside the box.
- The Wireless Stronghold Box (see www.paraben.com) is a must-see for any computer forensic laboratory working with wireless devices. This box, a Faraday cage, isolates any enclosed wireless device, making it a wireless write blocker. For added protection, all connections leading into the box are filtered.
- Wiebetech : These write-protect devices run the spectrum from field kits to RAID systems. Wiebetech products (see www.wiebetch.com) are also sold by the major forensic software makers, which adds to their credibility.
Media wiping equipment
Whether you complete one case per year or one case per day, you need to wipe the media you work with before you even start your case, to ensure that no cross-contamination between your cases occurs.
Forensic data wipers ensure that no data from a previous case is still present on the media. Most data wipers don’t erase existing data per se. They overwrite the data with either random binary strings or a repeating pattern of bits.
In addition to this capability, you need a report when the device is finished to prove that you wiped the drive beforehand. In a lab environment, you usually should have a dedicated device just for wiping your media to don’t use up valuable forensic tool resources spent wiping drives rather than analyzing evidence.
All the major computer forensic software and hardware manufacturers carry data wiping equipment. The chances are good that you can also purchase a dedicated data wiping unit wherever you bought your computer forensic software.
Just be wary of third-party data wiping tools that don’t have a way to verify the data wipe and don’t have a data wipe report function.
Recording equipment
Human perceptions being what they are, having an unbiased way to record events and objects is essential to computer forensic investigators. The choice of which device or devices you ultimately choose is based on your needs, but you must use some unbiased documentation method.
Using video or audio equipment to record important aspects of a case is a useful way to record your case’s unbiased view permanently. Using a video camera, you can repeatedly visit a crime scene to look for that single clue you missed.
You can document your methods directly by recording your work or even recording a computer screen’s output in a pinch.
Simply recording your thoughts is often best accomplished using a simple digital recorder that essentially acts as your personal note-taker!
You can find digital video cameras and audio recorders in any good retail electronics store, such as Best Buy or Radio Shack, and Internet retailers.
The basic models now available are more than enough to document all your case needs, as long as you carry extra batteries and data storage capacity.
 Cyber Security Magazine
Cyber Security Magazine




![How To Make a Website Fast and Safe [Guide]](http://cybersecuritymag.com/wp-content/uploads/2021/06/How-To-Make-a-Website-Fast-and-Safe-Guide-310x165.webp)


Hello, yup this post is truly pleasant and I have learned lot of things from it concerning blogging. thanks.|
You can certainly see your expertise in the article you write. The arena hopes for more passionate writers such as you who are not afraid to mention how they believe. All the time follow your heart.|
Yes are you sure
Nice post. Thanks for sharing it